
In the stillness of American night, a hidden threat seeped through the country’s digital veins. Hackers, allegedly linked to China’s Ministry of State Security (MSS), were slowly gaining control over America’s Internet arteries. They weren’t just stealing data, they were trespassing on the nation’s core, embedding themselves deep within networks operated by Verizon, AT&T, and Lumen. Known as “Salt Typhoon,” this covert team conducted a breach so extensive it bypassed even the most robust security frameworks.
This isn’t simply another data hack—it’s an urgent wake-up call for national security.
What Happened?
The Silent Infiltration: Inside Salt Typhoon’s Stealth Operation
The Salt Typhoon’s intrusion didn’t start with a bang but a whisper. For months, hackers reportedly navigated through America’s Internet infrastructure without leaving a trace. They found pathways into “lawful intercept systems” used by federal agencies to collect data on criminal and national security targets, allowing them a direct view of sensitive surveillance operations.
But it wasn’t until federal investigators from the FBI and Department of Homeland Security took a closer look that the true extent of this infiltration was revealed. This wasn’t just a breach, it was espionage on a level that alarmed the intelligence community. The sophistication of Salt Typhoon’s tactics suggests the involvement of a well-resourced, possibly state-backed agency, with China’s Ministry of State Security named as the prime suspect.
The Attack Unfolds: A Month-by-Month Timeline
Chronicle of a Breach: How Salt Typhoon Evaded Detection for Months
Timeline of Key Events:
- June 2024: Salt Typhoon initiates its infiltration, taking advantage of unpatched vulnerabilities within critical network routers.
- July 2024: Deeper access is established, allowing them to tap into lawful intercept systems and possibly review sensitive federal communications.
- August 2024: Data exfiltration is underway, with hackers slipping information through reconfigured routers, cloaked in invisibility.
- October 2024: The breach is finally discovered, prompting immediate federal response and a scramble to contain the damage.
Each step in this timeline reflects months of unchecked espionage that put America’s critical communication structures at risk.
The Stakes: How a Cyberattack Becomes a National Security Threat
What if foreign operatives accessed surveillance systems monitoring espionage, terrorism, or cybersecurity? Salt Typhoon’s intrusion holds dire implications: beyond federal target lists, it risks revealing classified communications and investigative targets, undermining counterterrorism and national security efforts.
This isn’t just theoretical damage, it had the Salt Typhoon gone undiscovered, they could have monitored America’s most critical investigations, silently observing government responses to threats or vulnerabilities in real time. Their ability to configure routers without detection demonstrates the advanced level of their access, raising serious questions about the security frameworks of America’s top telecom providers.
Response & Fallout: Verizon’s War Room
With the breach exposed, Verizon went on the defensive, setting up an emergency “war room” in Ashburn, Virginia. A nerve centre of experts from Verizon, the FBI, Microsoft, and Mandiant, the room is now filled with teams analysing data logs, retracing Salt Typhoon’s movements, and sealing vulnerabilities.
For those in the room, it’s a relentless, high-stakes race against time. Salt Typhoon’s breach has Verizon not only working to recover but also to prevent a repeat. The war room symbolises a frontline defence with a blend of technology and sheer vigilance, embodying Verizon’s urgent push to defend America’s digital borders.
The Diplomatic Dispute:
China Responds with Denial and Blame
In a now-expected move, China’s Embassy in Washington issued a sharp denial, calling the allegations “unfounded” and accusing the U.S. of “malicious disinformation.” Officials claim there’s no evidence linking China’s MSS to the breach, labelling the incident a calculated attempt to stoke anti-China sentiment.
This rebuttal is familiar, but it has left cybersecurity experts unconvinced. History paints a different picture with one of repeated cyber activity attributed to Chinese state-sponsored groups. These denials only reinforce the uncertainty surrounding Salt Typhoon’s motives and the broader agenda that may lie behind this breach.
What This Means for the Future of Cybersecurity
Future-Proofing Against the Next Salt Typhoon
Salt Typhoon’s breach is a call to rethink national cybersecurity. With even resource-rich giants like Verizon and AT&T falling prey to undetected infiltration, the need for a fortified cybersecurity approach is evident. America’s infrastructure can no longer afford complacency and new measures, that are more adaptable and proactive than ever before, are necessary.
For cybersecurity professionals, this incident underscores a critical reality: standard defence methods aren’t enough. A multi-layered, AI-enhanced, proactive cybersecurity framework is needed, capable of detecting and deterring even the most sophisticated threats.
How Can Organizations Stay Protected?
Strengthening the Defences
In response to breaches like the Salt Typhoon incident, companies, especially those handling sensitive information must take steps to strengthen their cybersecurity frameworks. Key actions include:
- Layered Security Systems: Adopt multi-layered defences that monitor and secure each part of the network, reducing points of vulnerability.
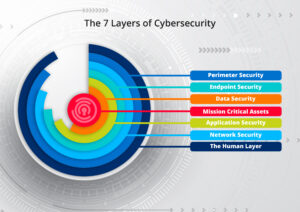
- Access Control and Monitoring: Enforce strict access controls and monitor network activity to quickly identify and address unusual behaviours.
- Regular Audits and Penetration Testing: Conduct frequent security assessments to proactively uncover and address potential weaknesses.

This breach reinforces that cybersecurity demands continual evolution to match the growing, adaptive nature of cyber threats.
Conclusion
A New Era of Cyber Vigilance
The Salt Typhoon breach is more than just a headline—it’s a call to action for every organisation to rethink and reinforce their cybersecurity. This incident highlights the need to stay one step ahead, constantly adapting to an evolving threat landscape.
At 2B Innovations, we’re dedicated to not only defending but also empowering organisations to thrive in a secure digital world. Our mission is to provide the tools, insights, and strategies needed to transform cybersecurity from a challenge into a strength. Let’s secure the future together, one layer of defence at a time.
Ready to turn resilience into your organisation’s greatest asset? Connect with 2B Innovations today.



