
The Healthcare sector’s cybersecurity faced a major blowout recently when the Rhysida ransomware gang claimed to be responsible for the catastrophic cyberattack on Prospect Medical Holdings.
The alleged attackers claimed to have stolen sensitive data amounting to a massive 500,000 social security numbers, corporate documents, and patient records.
Continue reading ahead to unfold the story.
Who, when, and how?
The target of the attack was Prospect Medical Holdings (PMH). It is a healthcare company in the United States, operating 16 hospitals in places like California, Connecticut, and Pennsylvania, along with a network of 166 outpatient clinics and centres.
The incident occurred on August 3, when the hackers proudly announced their takeover on the screens of the employees, with a note declaring that the network had been compromised and the devices had been encrypted.
Following is the note by Ransom, shown on Prospect Medical Holding’s devices:
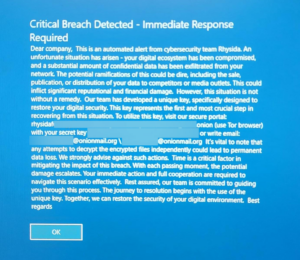
The Aftermath
The attack prompted PMH to take swift action. As a response, the hospital immediately shut down its IT networks to prevent the spread and scalability of the attack.
As a result, they were forced to resort to using traditional paper charts.
Despite the gravity of the situation, the hospital refrained from responding to the queries on the security incident. However, subsequent investigations by Bleeping Computer revealed that the Rhysida ransomware gang was responsible for the attack.
Latest Developments
Eventually, organisations like CharterCare, a network of PMH hospitals, recently stated that the systems are back in place and are running smoothly while the patient records are still in a restoration phase with ongoing efforts
They announced, “Work to input paper patient records used by our caregivers while our systems were down into our electronic medical record (EMR) system is ongoing.”
Regrettably, the employees of the hospital have had no communication regarding the potential compromise of their data in the attack. This lack of information raises concerns about the security of their sensitive information.
The Mastermind
The Rhysida ransomware gang was formed in May 2023. They quickly gained notoriety for their cyberattacks, particularly after the attack on the Chilean Army (Ejército de Chile). The group not only hacked into the company’s systems but subsequently leaked all of its sensitive data.
Earlier this month, the US Department of Health and Human Services (HHS) issued a warning announcing that the Rhysida gang is the mastermind behind the recent series of attacks on healthcare organisations.
The Ask
In this latest attack, the gang has made a brazen claim to have stolen data from PMH. The threat actors have demanded 50 bitcoins, which amounts to around $1.3 million. The threat clearly says that if their demand is not met, the stolen data will be sold.
According to their claims, they have managed to exfiltrate 1 TB of documents and 1.3 TB of SQL databases, which contain a vast amount of sensitive information, including over 500,000 social security numbers, passports, driver’s licences, corporate documents, and patient’s medical records.
They validated the same by sharing numerous screenshots of the stolen data on their data leak site. Some of the prominent documents include the letterheads of one of the PMH’s hospital networks, the Eastern Connecticut Health Network.
Moreover, the following was stated in their claim:
“They kindly provided: more than 500000 SSNs, passports of their clients and employees, driver’s licenses, patient files (profile, medical history), financial and legal documents!!!,”
Conclusion
Bleeping Computer has been vigorously trying to contact PMH with questions about the leaked data, but the hospital is abstaining from responding at this time.
The acuteness of this attack has prompted alarm about the increasing threat of ransomware attacks targeting healthcare organizations. The strategic moves and significant demands made by groups like Rhysida emphasise the urgency to address the situation, along with the need for robust cybersecurity measures and protocols to be followed not only in the healthcare sector but worldwide.



